CrococryptMirror 1.43a freeware
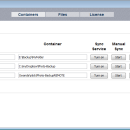
... mirrors complete folders to encrypted folders. The encryption algorithms that are used are AES and Twofish (256 bits, cascading). The keyfile is secured by a password using PKCS #5 (PBKDF2) with a SHA512/Whirlpool based HMAC using 100000 iterations and also AES and Twofish. Mirroring can be done manually (on-demand) or by using the sync service which detects directory changes on the fly. ...
| Author | Hissen IT |
| Released | 2021-06-16 |
| Filesize | 30.28 MB |
| Downloads | 662 |
| OS | Java, Win10 x32, Win10 x64, Win8 x32, Win8 x64, Windows 7 x32, Windows 7 x64, Windows Vista, Windows Vista x64, Windows XP, Windows 7 x64, Windows Vista x64, Windows 8, Windows 10 |
| Installation | Install and Uninstall |
| Keywords | encryption, file encryption, folder encryption, cloud encryption, cloud storage, aes, twofish, password, pbe, sha512, whirlpool, windows |
| Users' rating (26 rating) |
CrococryptMirror Free Download - we do not host any CrococryptMirror torrent files or links of CrococryptMirror on rapidshare.com, depositfiles.com, megaupload.com etc. All CrococryptMirror download links are direct CrococryptMirror download from publisher site or their selected mirrors.
| 1.43a | Jun 16, 2021 | Minor Update | Auto-Sync-Service fixed for Windows 10. For details go to the CrococryptMirror Homepage. |
| 1.42 | Feb 1, 2020 | Minor Update | Auto-Sync-Service fixed for Windows 10. For details go to the CrococryptMirror Homepage. |
| 1.41 | Apr 2, 2018 | Minor Update | Fix for Explorer View (WebDav) under Windows 10. For details go to the CrococryptMirror Homepage. |