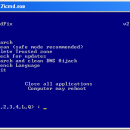
SmitfraudFix 2.423 freeware
It’s command-line based and it doesn’t need installation, nor is it complicated to use. The steps you need to take in order to clean your computer are described in the application’s main window: first off, you can perform a scan via the Search function, while the cleaning part of the whole process can undergo only in Safe Mode. ...
| Author | S!Ri |
| Released | 2015-10-14 |
| Filesize | 1.80 MB |
| Downloads | 461 |
| OS | Windows 2000, Windows 2003, Windows XP, Windows Vista, Windows Vista x64 |
| Installation | Instal And Uninstall |
| Keywords | Malware Scanner, Remove Malware, Malware, Malware, Malware Remover, Remover, Remover |
| Users' rating (37 rating) |
SmitfraudFix Free Download - we do not host any SmitfraudFix torrent files or links of SmitfraudFix on rapidshare.com, depositfiles.com, megaupload.com etc. All SmitfraudFix download links are direct SmitfraudFix download from publisher site or their selected mirrors.
| 2.423 | Oct 14, 2015 | New Release | [-HKEY_CURRENT_USERSoftwareColdWare] [HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionRun] "WinProtect"=- |