Svchost Process Analyzer 1.3 freeware
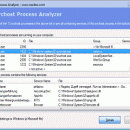
... directory. The Svchost.exe processis often misused by spyware, Trojans or worms. ...
| Author | A. & M. Neuber Software |
| Released | 2017-02-16 |
| Filesize | 523 kB |
| Downloads | 639 |
| OS | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Installation | No Install Support |
| Keywords | svchost, svchost.exe, conficker, configer worm, svhost, scvhost, _svchost.exe |
| Users' rating (21 rating) |
Svchost Process Analyzer Free Download - we do not host any Svchost Process Analyzer torrent files or links of Svchost Process Analyzer on rapidshare.com, depositfiles.com, megaupload.com etc. All Svchost Process Analyzer download links are direct Svchost Process Analyzer download from publisher site or their selected mirrors.
| 1.3 | Nov 30, 2015 | Major Update | Windows 10 compatibel, small bugs fixed |
| 1.1.0.44 | Jan 25, 2013 | Major Update | small bugs fixed |
| 1.1 | Jan 25, 2013 | Major Update | small bugs fixed |