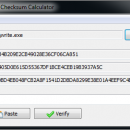
File Checksum Calculator 1.2 freeware
A standalone utility that generates and verifies cryptographic hashes in MD5, SHA-1 and SHA-256. Cryptographic hash functions are commonly used to guard against malicious changes to protected data in a wide variety of software, Internet, and security applications, including digital signatures and other forms of authentication. ...
| Author | VOVSOFT |
| Released | 2018-12-28 |
| Filesize | 2.22 MB |
| Downloads | 163 |
| OS | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows Vista, Windows Vista x64 |
| Installation | Install and Uninstall |
| Keywords | md5, sha1, sha256, checksum, verify |
| Users' rating (19 rating) |
File Checksum Calculator Free Download - we do not host any File Checksum Calculator torrent files or links of File Checksum Calculator on rapidshare.com, depositfiles.com, megaupload.com etc. All File Checksum Calculator download links are direct File Checksum Calculator download from publisher site or their selected mirrors.
| 1.2 | Dec 28, 2018 | Major Update | Implemented multi-threaded calculation, faster now. |
| 1.1 | Sep 12, 2018 | Major Update | Drag and drop supported. Improved UI. |
| 1.0 | Aug 16, 2018 | Major Update | Fixed bugs. |