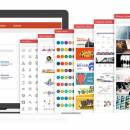
iSlide 6.2.0.3 freeware
... Library 9. Vector Library 10. Join Images 11. Security Export 12. ZoomIt ...
| Author | iSlide Network Technology |
| Released | 2021-06-25 |
| Filesize | 58.00 MB |
| Downloads | 287 |
| OS | Windows 7, Windows 7 x64, Windows 8, Windows 8 x64, Windows 10, Windows 10 x64 |
| Installation | Instal And Uninstall |
| Keywords | MS PowerPoint Add-in, MS Office Enhancement, Professional PPT Design, PowerPoint, Presentation, PPT, Work, Office 365, iSlide, slide, PPT, ppt, font, theme, design, powerpoint plugin |
| Users' rating (45 rating) |
iSlide Free Download - we do not host any iSlide torrent files or links of iSlide on rapidshare.com, depositfiles.com, megaupload.com etc. All iSlide download links are direct iSlide download from publisher site or their selected mirrors.
| 6.2.0.3 | Jun 25, 2021 | New Release | |
| 6.2.0.2 | May 12, 2021 | New Release | |
| 6.0.0.3 | Jan 8, 2021 | New Release |