AUTHENTiC The Checksum Calculator 1.0.1 freeware
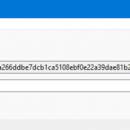
AUTHENTiC is a modern (and free) tool for checksum verification. Featuring a convenient GUI and a drag and drop interface, it is both powerful and user-friendly, quickly letting you verify the integrity of files. The current version supports 15 different hashing algorithms. You can validate files with: MD5, SHA1, Adler-32, Blake2b, Blake2s, CRC32, RIPEMD-160, SHA-224, SHA-256, SHA-384, SHA-512, SHA3-224, SHA3-256, SHA3-384 and SHA3-512. ...
| Author | WhiteLynx Development |
| Released | 2019-09-27 |
| Filesize | 6.78 MB |
| Downloads | 138 |
| OS | Win2000, Windows XP, Windows 7 x32, Windows 7 x64, Windows 8, Windows 10, WinServer, WinOther, Windows 2000, Windows 2003, Windows Server 2000, Windows Server 2003, Windows Server 2008, Windows Server 2008r2, Windows Server 2012, Windows Tablet PC Edition 2005, Windows Media Center Editi |
| Installation | Install and Uninstall |
| Keywords | checksum, hash, hashing, file, hashes, authenticate, validate, authenticity |
| Users' rating (28 rating) |
AUTHENTiC The Checksum Calculator Free Download - we do not host any AUTHENTiC The Checksum Calculator torrent files or links of AUTHENTiC The Checksum Calculator on rapidshare.com, depositfiles.com, megaupload.com etc. All AUTHENTiC The Checksum Calculator download links are direct AUTHENTiC The Checksum Calculator download from publisher site or their selected mirrors.
| 1.0.1 | Sep 27, 2019 | New Release | First Public Release |